Small businesses need to do whatever they can to stay competitive and efficient. Today, we want to share some of the most transformative technologies that can help your organization keep up with the rapidly changing business landscape. These include artificial intelligence, cloud computing, and cybersecurity solutions.

KB Technologies Blog
KB Technologies has been serving the Deerfield Beach area since 2002, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
0 Comments
Running a small or medium-sized business means wearing many hats. But is "Chief IT Firefighter" one you want to wear? Constant tech issues, cybersecurity worries, and wondering if your IT is holding you back. Sound familiar?
For many local businesses, IT feels more like a necessary burden than a strategic tool.
Make no mistake about it, small businesses are being targeted. Thankfully, there are advanced IT security tools that are more accessible to lower-revenue organizations than ever, allowing small businesses to defend themselves like large enterprises. Let’s go into some of the top tools that are helping small businesses stay safe.
Business depends on technology; this fact is what drives businesses to adopt new solutions from vendors and providers around the world. If your business needs to acquire new technology solutions to maintain operations, you’ll likely be working with third parties to make it happen. Today, we want to discuss the idea of business contracts and how to get the best deal from IT vendors you possibly can.
It’s easy to see all the reasons why you should make data regulations and compliance a priority. After all, you want to ensure you don’t violate the trust and security of your customers, as well as the integrity of your operations. If you make even one mistake, it could spell legal trouble for your business, as well as financial losses and loss of reputation.
Data loss can be from a cyberattack, hardware failure, or just plain bad luck. Either way, it is a real threat to your business. You can hedge against it by having solid data backup strategies in place. Today is World Backup Day, so we thought we’d go through some ways to build a data redundancy platform that will keep you from being left scrambling should disaster strike.
Do you have someone on your staff who can handle most IT-related issues for your business? If not, we’re sure your organization feels it in more ways than one. The issues that come from not having IT help are only made more frustrating when it comes time to find IT help—particularly if you’re committed to getting a technician on-premises.
How much your business should spend on cybersecurity largely depends on a variety of factors, and you cannot lump yourself in with just any other business. The same IT budget will go to different lengths for different businesses. Your typical small business, for example, will not need the same level of security as a serious mega-corporation. But this doesn’t diminish the importance of cybersecurity spending; we’ll tell you why.
In the grocery store, we’re given the estimated date that the food we’re buying will turn, helping us to make more informed decisions about what we are purchasing and the quality therein. Wouldn’t it be nice if the same could be said about the technology our businesses rely on?
Well, moves are being made to establish this as the standard in tech as well.
We've officially reached the point where humans have to prove they're, well, human just to access websites. One of the most common ways to do this? CAPTCHA. CAPTCHA stands for Completely Automated Public Turing test to tell Computers and Humans Apart. It might sound long-winded, but the idea is simple. Computers still struggle to crack these tests, making them a solid way to block bots. But why exactly do they work so well?
Our phones, laptops, smart home devices, and even our cars are packed with data about our lives. But what happens when law enforcement wants access to that information? Whether you're an individual just trying to keep your personal data safe or a business owner handling customer information, here’s what you need to know.
Automation makes sense from an operations standpoint, and people see this despite the many who advocate for scaling back to save jobs. For every task that can be completed, however, less than half can be automated. When you consider all the tasks that a human might be responsible for at their job, that number further dwindles, resulting in surprisingly few jobs that can be fully automated by artificial intelligence. Today, we want to look at reasons why you shouldn’t implement automation for certain tasks and why working with humans is still the right call for many.
While it’s impossible to catch a glimpse of the future, we can make some educated guesses as to what we think it’ll look like. On the business IT front, we can use trends and current events to look at what we can expect. This will help you plan out your technology-related efforts throughout the remainder of the year.
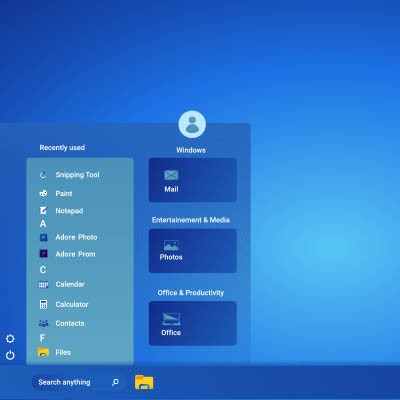
Last month, we touched on how Windows isn’t necessarily the standard in the home as in the modern office… and therefore, how many users may not necessarily be as familiar with the operating system as some might hope. In light of how vital familiarity with Windows is in the modern workplace, we wanted to share how Windows 11 works.
To continue this exploration, we wanted to take a closer look at the Start menu, which can be found on the toolbar.
Technology touches nearly every facet of our lives. They make smart toothbrushes if you want it to touch every facet of yours. As a result of being such a tech-driven society, there were opportunities for businesses to set themselves apart by appealing to the incendiary demand for more. Today, we just wanted to point out that, while it has happened throughout the information age, today’s top tech companies are some of the most powerful ever.
Reach Out Today!
Mobile? Grab this Article!
Tag Cloud
Malware
Hosted Solutions
Cloud
Saving Money
Productivity
Data
Best Practices
Network Security
Collaboration
Privacy
Current Events
Email
Tip of the Week
Internet
Hackers
Users
Disaster Recovery
User Tips
Workplace Tips
Google
IT Services
Phishing
IT Support
Business
Workplace Strategy
Technology
Efficiency
Ransomware
Hardware
Managed IT Services
Business Computing
Backup
Data Recovery
Cybersecurity
Quick Tips
Security
Innovation
Microsoft
Mobile Device
Software
Latest Blog
Small businesses need to do whatever they can to stay competitive and efficient. Today, we want to share some of the most transformative technologies that can help your organization keep up with the rapidly changing business landscape. These include artificial intelligence, ...
Latest News
KB Technologies is proud to announce the launch of our new website at http://www.kb-it.com. The goal of the new website is to make it easier for our existing clients to submit and manage support requests, and provide more information about our services for ...