We've officially reached the point where humans have to prove they're, well, human just to access websites. One of the most common ways to do this? CAPTCHA. CAPTCHA stands for Completely Automated Public Turing test to tell Computers and Humans Apart. It might sound long-winded, but the idea is simple. Computers still struggle to crack these tests, making them a solid way to block bots. But why exactly do they work so well?

KB Technologies Blog
KB Technologies has been serving the Deerfield Beach area since 2002, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
0 Comments
The Internet offers boundless opportunities… for those willing to take a few risks. Data privacy is a hot-button issue regarding the Internet, as most websites and social media platforms can track your activity and sell it to advertisers (or even train AI systems). Here’s how you can keep this to a minimum.
For years, you've heard about the growing role of technology in healthcare, promising to stabilize costs, improve access, and personalize care delivery. As these innovations take hold, however, they also raise serious concerns about data privacy. Today, we’ll explore some of the technological advancements in healthcare and their implications for patient data privacy.
It’s no secret that data security is of paramount importance, with phishing and ransomware making weekly appearances in the news cycle at this point. You need to prioritize your business data’s privacy. Otherwise, you’re apt to suffer from your data being accessed without authorization and all the consequences that come with this outcome. Today’s criminals are very capable, which makes it challenging to protect yourself.
Here, we’ve put together some essential strategies to make it easier.
Every organization must implement a baseline of cybersecurity measures, encompassing elements such as firewalls, antivirus software, VPNs, encryption, and centrally managed security policies. However, the evolving landscape of cyberthreats means that modern cybercriminals are adept at circumventing these defenses.
If you asked your workers to provide their feedback on digital monitoring, do you think they would be in favor of it or against it? A survey indicates that perhaps digital monitoring is not the controversial topic it was once considered in the workplace, at least to a certain extent. The catch? Monitoring has to give them opportunities to improve their job performance, and it shouldn’t get in the way of them doing their jobs.
When you think of the words “compliance” and “your business” together in the same sentence, does the idea strike fear and dread into your heart? Businesses that fail to remain compliant could suffer severe penalties. It’s not always clear-cut what compliances your organization might need to adhere to, but we can help you implement the technology to ensure you remain compliant.
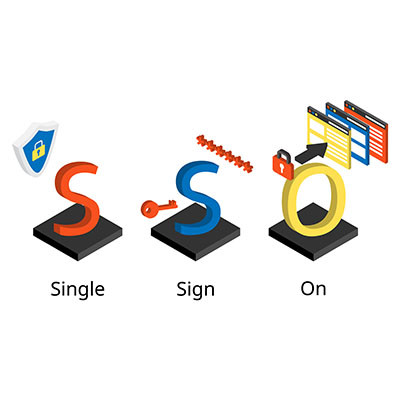
One of the ways that businesses have approached the issue of having to log into multiple different accounts, applications, websites, and services is through the use of single sign-on solutions. It’s a common technology that you might see just about every day, but how does it work, and what kind of security can you expect from it?
Today’s blog might seem a bit simple, and that’s because it is. Your network security is going to play a huge part in the operations and functionality of your business, whether you realize it or not. In fact, your network security might be the only thing keeping your business in proper working order. We’re going to discuss some of the less-obvious reasons why security is beneficial for businesses like yours.
Cyberwarfare has continued to evolve in sophisticated ways, and while security researchers try their best to keep up, hackers are always trying to outdo them. One example of such attacks, which are often sponsored by government agencies, is a recent attack on the United States and Israeli technology sectors, which have become the target of password spraying campaigns.
If we told you that it is possible for others to hire hackers to launch attacks against your business, would you believe it? Well, we hope so, because it is very possible and more common than you might think. Comparitech launched an investigation into the average prices of various hacking services on the Dark Web, and you might be surprised by how affordable and accessible they are. This is just more reason to take network security seriously.
When it comes to network security, there are a lot of complex solutions that solve multi-faceted issues, some so mind-boggling in scope that it is simply overwhelming. Then there are the small-scale solutions that you can implement on a day-to-day basis that can make significant changes over time. Locking your computer is one of these tactics, and it should not be overlooked in your security strategy.
While most people may be most familiar with the concept of the blockchain thanks to cryptocurrencies—particularly with the recent behaviors of some coins—this first application of the blockchain has blossomed into many others with great potential. Let’s go over what blockchain technology is, how it works, and how it can benefit businesses of all kinds.
There are a lot of cyberthreats out there… too many for the modern business to avoid them all. While employing best practices may greatly reduce your chances of being breached and having data stolen from your network, they can also help you determine how a breach occurred and how your data was stolen. While there is no such thing as perfect cybersecurity, there are a few strategies you can lean on to strengthen yours.
Smart assistants are one of the most intriguing and confounding technologies developed over the past decade. At the time of this writing, over 150 million smart speakers are in 60 million homes in the United States, when you add in the smart assistants available on mobile devices and other various smart devices, you’re talking a billion people actively using some type of smart assistant. Over the past couple of years, you’re beginning to see these assistants being used more for business and this has made certain security-minded people a little weary of them. Let’s take a look at some of the security questions surrounding the smart assistants.
It may not be a surprise to you that hackers and other scammers are trying to get between you and your stimulus money. Using the COVID-19 pandemic to prey on unsuspecting or ill-prepared people, they have already made off with more than millions of the $290 billion that the U.S. government has earmarked for its citizens. Let’s look at how you can avoid being another unfortunate victim of the modern cybercriminal.
Social media has brought about a massive shift in the way people interact. Today we share our opinions, photos, and videos; and, we can even choose our dates by swiping right or left. With social media, people share moments, opinions, and other information, but is all this sharing actually setting people, and the organizations they interact with, up for failure? We’ll take a look at social media privacy concerns and potentially hazardous practices that could exacerbate the problems further.
Email is (and has been) a prime method of communication for businesses of all sizes. With email comes a whole slew of issues that are essentially synonymous with the technology; spam, information overload, phishing, and information privacy. Even Florida small businesses that only do business locally are at risk of these issues. Personal email accounts are equally at risk. Employing proper precautions and practices whenever communicating via email is very important to prevent the risk of security compromises, monetary loss, and even legality issues.
Reach Out Today!
Mobile? Grab this Article!
Tag Cloud
Data Recovery
Ransomware
Microsoft
Users
Email
Collaboration
Data
Innovation
Google
IT Services
User Tips
Network Security
Quick Tips
Mobile Device
Security
Hosted Solutions
Best Practices
Technology
Cybersecurity
Disaster Recovery
Hardware
Malware
Tip of the Week
Cloud
Current Events
Hackers
Workplace Tips
Business Computing
Software
Managed IT Services
Privacy
Workplace Strategy
Business
Saving Money
Phishing
Internet
Efficiency
Backup
Productivity
IT Support
Latest Blog
Small businesses need to do whatever they can to stay competitive and efficient. Today, we want to share some of the most transformative technologies that can help your organization keep up with the rapidly changing business landscape. These include artificial intelligence, ...
Latest News
KB Technologies is proud to announce the launch of our new website at http://www.kb-it.com. The goal of the new website is to make it easier for our existing clients to submit and manage support requests, and provide more information about our services for ...